Internal HR documents have been leaked, according to the British Library, which was the target of a ransomware attack that rendered its computer systems, website, phone network, and common Wi-Fi inoperable for more than three weeks.
Readers seeking access to books and manuscripts are now required to make requests from human catalogs at the library’s Kings Cross building, which it describes as a “very limited service,” according to the Rhysida ransomware group.
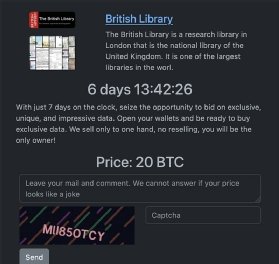
The hacking group held a seven-day auction on its website on Monday, November 20, offering information it claims to have taken from the British Library.

” Seize the chance to bid on special, unique, and impressive data with just 7 days on the clock.” Be prepared to purchase special data by opening your wallets. You will be the only owner because we just sell to one hand; there is no reselling.
Rhysida has listed a bid price of 20 bitcoins ( roughly £600,000 ) to buy the data on the dark web, but if no one is interested, it may still be published.
Rhysida’s claims have not received any public comment from the library, but it has reported that some HR information appears to have been leaked from its inner HR files in an update on X, previously known as Twitter.
On Rhysida’s Tor website, a low-resolution image appears to display passports and other employment-related documents.
The library stated in an update,” We have no evidence that our users ‘ data has been compromised.” However, we advise changing your password as a preventative measure if your English Bank login is already used elsewhere.
Since the library reported that a “technical issue” had affected its IT systems on October 28, it has experienced major disruption to its locations in St Pancreas, London, and its annex in Boston Spa, Yorkshire. On November 14, it confirmed that it had been the target of a ransomware attack.
The library is only allowed to accept cash payments because it lacks a functioning website or phone service. Updates from it confirmed that it is conducting a criminal investigation in collaboration with the Metropolitan Police and the National Cyber Security Center (NCSC ).
Requested price for data from the British Library
The price Rhysida demanded for the American Library data, which was 50 bitcoins for data taken from Prospect Medical Holdings in August 2023, was fairly high, but not the highest, according to Victoria Kivilevich, director of threat research at security firm KELA Cyber Threat Intelligence.
” As can be seen from looking at their website, the Rhysida group does n’t always succeed in selling the data they try to auction. For instance, they just attempted to charge 10 bitcoins for data taken from Azienda Ospedaliera Universitaria Integrata di Verona, but the information is presently freely accessible on their website, proving there were no buyers, she said.  ,
The malware, which was first discovered in May 2023, is offered as ransomware as a service to criminal organizations, who then split the proceeds with the owners, according to an advisory note from the FBI and the US Cybersecurity and Information Structure Agency ( CISA ) last week.
Hackers use VPNs to gain access.
Criminals frequently use well-known vulnerabilities, like ZeroLogon, to access afflicted computer systems.
Attackers have also compromised credentials to access virtual private networks (VPNs ), especially in places where two-factor authentication is not required by default.
By demanding a ransom payment to decrypt victims ‘ data and threatening to publish the data if not, groups using the malware engage in “double extortion.”
Victims are sent a PDF ransom note with instructions on how to get in touch with the group on the black web as well as an individual reference code for each company attacked.
The Chilean Army was one of their first and significant targets, according to Jim Walter, top threat researcher at SentinelLabs, which has produced an analysis on Rhysida. Additionally, they have struck government targets in the Dominican Republic and Kuwait.
An attack on the American Library is within the group’s purview because Rhysida has targeted organizations in the education and scientific sectors in addition to government entities, he continued.
Rhysida usually employs “living off the land” techniques to take advantage of network administration tools included in the Windows operating system, according to Marcelo Rivero, top malware research engineer at Malwarebytes. By blending in with regular network activities, attackers can avoid detection in this way.  ,


